Have a try! An awesome freeware application for computers..
Download here.
Information about resetting and configuring Mobile phones (Java, Android, Symbian etc), educational articles especially for programming in C, C++ and Java and more about Computers and operating systems
Mad Mouse Prank Application Software - Trick Your Friends
 Mad Mouse! Mouse goes mad? Not literally. What would you think if your mouse pointer is moving You can either download the app and give it to your friends. Or you can use the share buttons below to share the app with friends.
Mad Mouse! Mouse goes mad? Not literally. What would you think if your mouse pointer is moving You can either download the app and give it to your friends. Or you can use the share buttons below to share the app with friends.on its own? And what if not responding to your mouse's motion? Normally, one would assume that there is some problem with the mouse, especially some hardware problem. Right? You can trick your friends with an application which when opened, takes control of the mouse pointer. Just use the share buttons provided below to trick your friends. After running the mouse pointer mad on the screen for 2 or 3 minutes, the app will deliver a message, "you are pranked".
Click to download the app.
This app is based on java 1.8 jre. Therefore, the computer should have jre 1.8 or later. To get java 1.8 or later. Click here.
Add links for sharing using below buttons
Share to trick your friends






Share the trick with your friends







Computer Networks Modulewise Short Notes Free PDF and Doc Download
Welcome. I have uploaded some short notes (lecture notes) and slides for CN (Computer networks). Computer Networks is a subject taught for Computer Science and Engineering Branches and Information technology Branches. The notes for Computer networks are available for download. There are different notes from different sources. We have also included slideshows (slides). The note full set is complete. You can compare and study. Computer networks slides are specially mentioned as slides. MGU (MG university) Computer networks syllabus is available here.
Module 1:
Network requirements, Network Architecture, Layering and Protocols, OSI Architecture, Internet Architecture, Performance - bandwidth and latency, Delay bandwdith product, high speed networks.
Note Full Set
Other notes:
Module 2:
Direct Link network, hardware Building Block, Framing - Byte Oriented protocol, Bit oriented protocol, Clock based framing, Reliable transmission- stop and wait, sliding windows, Ethernet (802.3)- physical properties, Access protocol, wireless-bluetooth, wifi, Wimax
Other notes:
Module 3:
Packet switching-switching and forwarding-Datagram, virtual circuit switching, source routing bridges and LAN switches - Learning bridges, Spanning tree algorithms, Broadcast and multicast, Limitations of bridges, simple internetworking - service model, global address, datagram forwarding in IP, address translation, Routing - network as graph, distance vector, link state, matrix.
Other notes:
Module 4
End to End protocol, simple de-multiplexer, reliable byte stream, TCP - Issues, segment format,connection establishment and termination, sliding window revisited, triggering transmission,, adaptive retransmission, RPC- fundamentals, TCP congestion control, - additive increase, slow start, fast retransmit and fast recovery, congestion avoidance mechanism, DEC bit, Randomearly detection bit, source based congestion avoidance.
Other notes:
Module 5
Applications -WWW, Email, name service, network management, web services custom application protocol, generic application protocol, overlay networks - peer to peer networks.
Other notes:
Labels:
BE
,
BTech
,
computer networks
,
Computer Science
,
doc
,
engineering
,
free download
,
information technology
,
IT
,
lecture notes
,
modulewise notes
,
notes
,
pdf
,
ppt
,
slides
How Block Websites on a Windows Computer
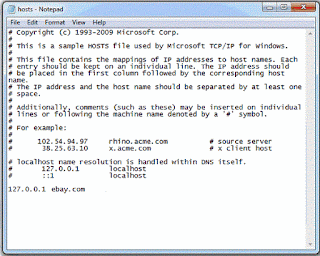
We will see how to block websites on a computer. There is a fine trick to block websites on any computer. This is done by editing the hosts file. The 'hosts' file is used to map host names to given IP addresses. The 'hosts' file is a plain text file that can be edited using text editors. Each line is a redirection entry. Each line should be an IP address followed by a space followed by a host name. When any application software (including browsers) try to connect to a host name (or website) which has an entry in the 'hosts' file, instead of using the domain name service, the IP address is taken from the corresponding entry in 'hosts' file. Then the connection goes to that IP address.
So, if we want to block any website, we only need add an entry for that website in the hosts file with a different IP address. By 'different IP address', i mean any IP other than the original IP of the website. The IP 127.0.0.1 is IP of your own computer. It is called loop back address. You can use this IP to block any website. If you use this IP, the application will try to connect to your own computer on its attempt to access the blocked website and thereby will fail to load the website.
hosts File in Windows
In Windows 7, Windows 8 or 8.1 and Windows 10, the hosts file can be found in the folder:
C:\Windows\System32\drivers\etc\
Here, C: is Windows installation drive.
How to Edit 'hosts' File in Windows - Why to Edit It?
 |
| Windows host file screenshot |
Why use hosts file
As said earlier, the hosts file is used to map domain name (actually host names) to IP some address. The file contains many lines starting with # symbol. Those lines are comments. Within the comments you can see some examples showing how to use the hosts file. Each line (not comments) should contain an IP address followed by a space and a host name. The format is:
IP_address<space>Host_name
When you access the host with given host name using your browser or any other application, before looking for the host name in your Internet Domain Name Service (DNS), your computer looks in the hosts file first. If there is an entry for the hostname the IP address provided in its line is used to access the website.
In the example given by Microsoft, rhino.acme.com is redirected to 102.54.95.97. Similarly x.acme.com is redirected to some other IP.
Why 127.0.0.1 ?
127.0.0.1 is the loop back address. It is the IP of your own computer. It is corresponding IP for localhost. localhost is the host name used to represent the computer from which we are accessing network (means our own computer). It is same to use 127.0.0.1 or localhost. But you cannot redirect a host name to another host name in hosts file. You should use an IP. When you redirect some host name to 127.0.0.1, actually you are redirecting the access to your own computer, which means blocking access to that host name
Uses of hosts file
As we have seen, the uses of hosts file are:
- Redirecting one host (or website) to another using an IP
- Blocking websites completely (by redirecting to 127.0.0.1)
Some people use hosts file to prevent pirate software accessing the vendors website to avoid auto update. We won't recommend piracy. Find a free software alternative if you cannot afford buying it.
Torrent or BitTorrent - What is it, How it Works, All about Torrents
Difference between Torrent and BitTorrent
Actually, there is no difference between BitTorrent and torrent. The name of this technology is BitTorrent. Later it became popularly known as torrent. People often use both torrent and BitTorrent interchangeably.
What is Torrent and How it Works
Now, we see what is torrent or BitTorrent. If you are not well versed with network terminologies, the simplest answer is,
Torrent or BitTorrent is a way of file sharing over internet, especially for large files.And if you think you know something about networking, it can be defined this way:
BitTorrent is a protocol that enables of peer-to-peer file sharing that is used to distribute large amounts of data over the Internet.
How to Root Your Samsung Galaxy S4 Android Phone
Root Samsung Galaxy S4:
Everyone roots their Android phones. Samsung, Sony, HTC, every android phones are now being rooted. And you want to root your Samsung Galaxy S4 phone? Yeah, that is why you are in search of tutorial on how to root Samsung Galaxy S4. Okay, but there are some requirements.
Things to remember before you root your phone:
- Rooting will nullify the warranty of your phone
- If your phone bricks, we are not responsible for it.
Requirements to root Samsung Galaxy S4
The main requirements to do rooting of your Samsung S4 phone i9500 or i9505 are:- USB Data Cable
- Download Odin flashing software
- Download USB Driver file
- Download Root File
C Programming Previous Year Question Paper for Automobile, Mechanical, Production or Metallurgy
Here i have uploaded the previous year (2014 November) question paper of Programming in C for Third semester for Automobile Engineering, Mechanical Engineering, Production Engineering or Metallurgy branches under MG university BTech course.
Course : B.Tech Engineering (degree)
University: MG university (Mahatma Gandhi university) Kottayam, Kerala
Department or branch: Automobile Engineering, Mechanical Engineering, Production Engineering or Metallurgy
Course : B.Tech Engineering (degree)
University: MG university (Mahatma Gandhi university) Kottayam, Kerala
Department or branch: Automobile Engineering, Mechanical Engineering, Production Engineering or Metallurgy
Labels:
$studymat
,
2014
,
Automobile
,
B TEch
,
B.Tech
,
BTech
,
c language
,
C programming
,
calicut
,
download
,
engineering
,
mechanical
,
MG University
,
pdf
,
previous
,
production
,
question paper
,
s3
,
semester
,
third
C Program to Simulate Round Robin CPU Sceduling Algorithm
The round robin CPU scheduling algorithm is simulated using C program. The time slice or time quantum is read from the user.
Program:
#include<stdio.h>
struct process{
Program:
#include<stdio.h>
struct process{
Labels:
$ccpp
,
algorithm
,
c program
,
code
,
compiled
,
CPU scheduling
,
lab
,
operating Systems
,
OS lab
,
round robin
,
simulate
,
simulation
,
source code
Subscribe to:
Comments
(
Atom
)